By Andrew Le Gear
During July of 2018, the gas price for Ethereum rose by 500% to an Ether price of 100GWei (average), but some peaks of 150Gwei~ were seen. This rise was unprecedented. On closer inspection of the block range 0x5AC91B to 0x5B009B where the rise occurred we see over 80,000 transactions centred around a single ERC-20 contract called iFishYunYu (0x98b4ca8bd52e4ed1f28d3f30d9f567d1166c9483). These transactions were submitted with gas prices more than 150GWei – staggeringly expensive given that the normal expensive “fast” gas price is about 20GWei.
iFishYunYu appeared to have no obvious real-world value. Normally an ERC-20 is linked to additional meta-data describing an asset or platform that it represents utility or ownership of. This meta-data usually includes source code of the contract and links to the real-world company presence offering the token. No such supporting documentation existed with iFishYunYu.
Forums associated with the Ethereum network levelled accusations of attempting to inflate the perceived volumes of the contract to fraudulently gain a listing on token exchanges, or a bad actor deliberately attempting to prove a point on the vulnerability of the Ethereum network (here). What is certain is that at a high gas price of 150 Gwei, the 80k+ transactions executed amounted to a very expensive endeavour totalling about $285,000 in transaction fees for a token of no obvious value.
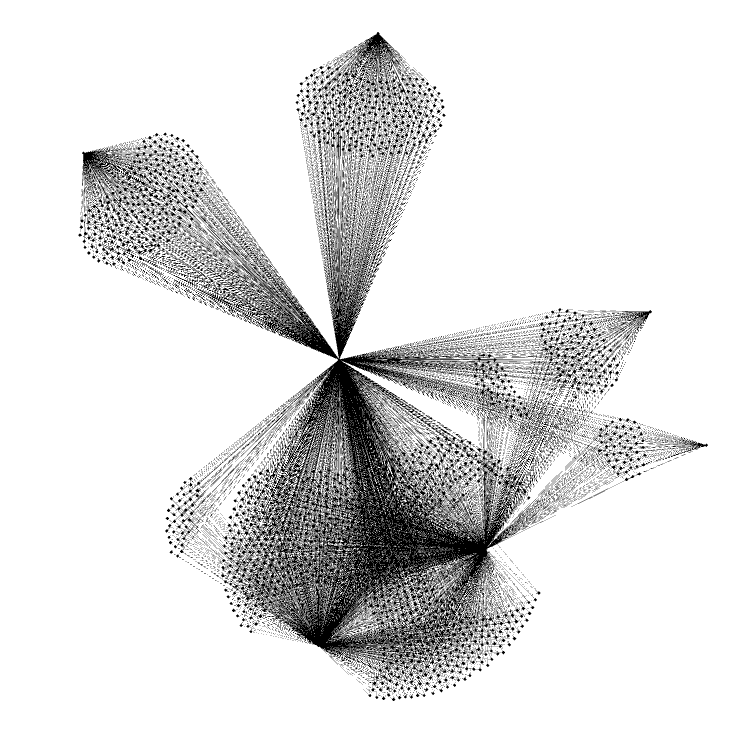
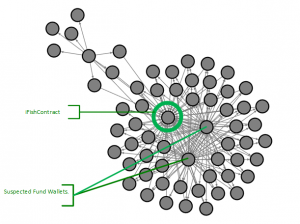
We wondered would there be a more general means of detecting attacks like this. We suspected that whoever staged the attack would be funding thousands of wallets to perform simultaneous transactions, and that the funding would have originated from a single, or small number of sources. So, we postulated that if we could detect the circular movement from “fund wallet” to “attack wallets” to the iFishYunYu contract and back we would reveal the culprits for the iFishYunYu attack and give us a forensic tool for identifying future attacks.
We scraped the transaction data for iFishYunYu from Ethereum in the block range mentioned and imported it into a graph DB (Gremlin and Apache Tinkerpop) and queried it for cycles originating with the iFishYunYu contract.
The output was startling! Every transaction to iFishYunYu was part of a cycle and all funds for transacting on iFishYunYu originated from just 8 wallets:
- 0x8c1b1473cffc7ff621c8b50316c90a0b8b32558a
- 0x91a79c71a702942135814a6746d71f2ef0ae0262
- 0x45f64a7148d1cfeded427dd4380b458877e7ce56
- 0xa9a0f46f8e24a7f9153333b50659a2e7e6875ecc
- 0xa6d73d0e15f811e6945bc270c5825918da2645b1
- 0x7c1cff9e521cffba0c45859dbd274982c44c45b3
- 0x4d1167c167a080d6b973561a3b7683cc998108e1
- 0xe47093061140f7e2e8b81b78bfc322dc70b50259
Here is are the graphs showing cycles of length 4 and 3 respectively.
There is no denying the suspicious nature of the source of these transactions. More important than the actual culprit wallets is the pattern – Now we have the means to see an attack emerging in progress in real time. Looking forward to the next attack! 😊